The security bug must be original and previously unreported.
The security bug must be found under the "nervosnetwork" GitHub page , not the code of a third party.
You must not have written the buggy code or otherwise been involved in contributing the buggy code to the Nervos project.
You must not be an employee, contractor, or otherwise have a business relationship with the Nervos Foundation or any of its subsidiaries.
You can start or fork a private chain for bug hunting. Please respect the CKB mainnet and testnet and refrain from attacking them.
Public disclosure of a vulnerability makes it ineligible for a bounty.
The bounty rewards are subject to standard KYC requirements and vetting in order to be eligible.
Determinations of eligibility, score, and all terms related to an award are at the sole and final discretion of the Nervos Bug Bounty team.
The total initial rewards issued during the Nervos Bounty Program is $1M USD.
The program starts on Oct 22, 2019 and will end when the 1M rewards have been paid out.
We have adopted the OWASP model; the rewards are determined by the severity of the bug.
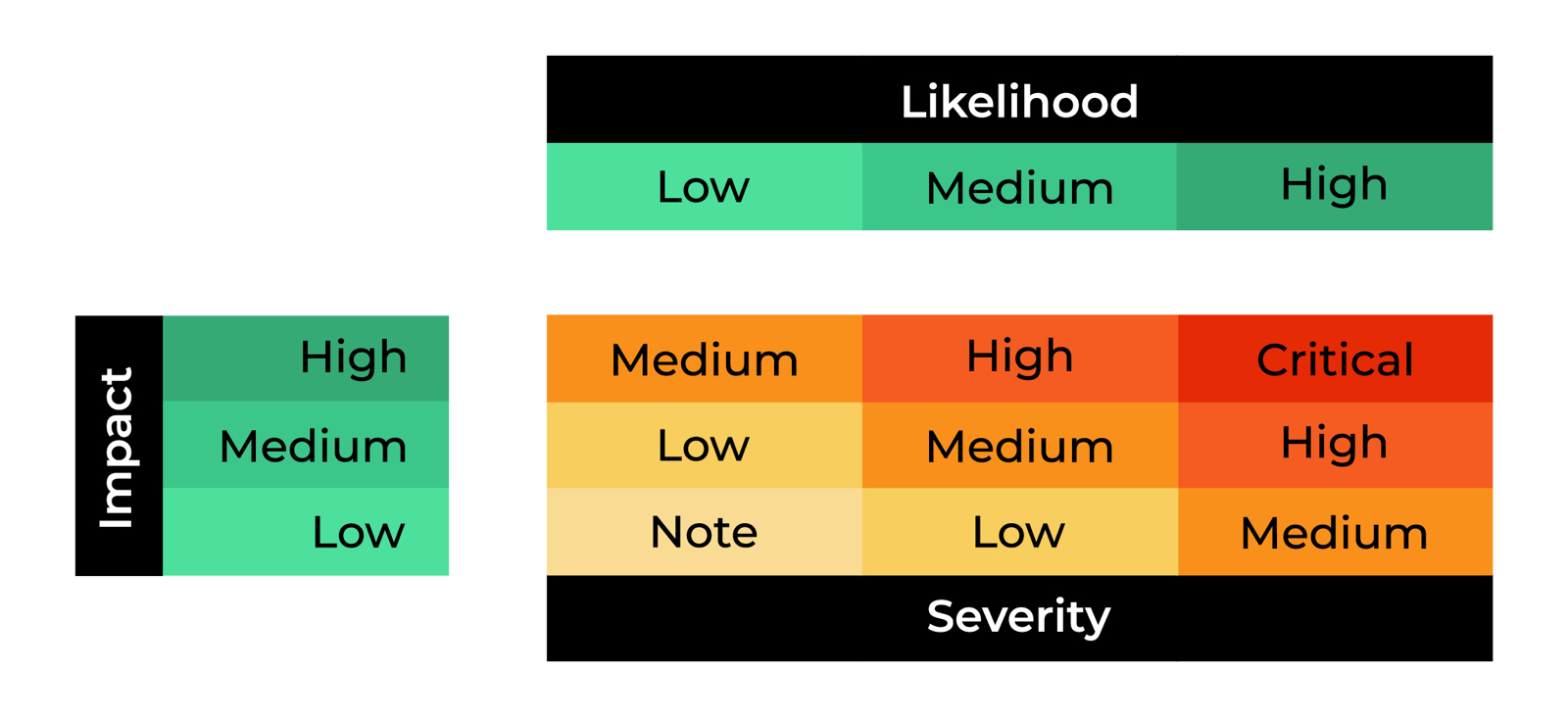
In addition to severity, Nervos Bounty Program considers a number of other variables in determining rewards, including (but not limited to):
Quality of description.
Quality of reproducibility, such as test code, scripts and detailed instructions.
1 point currently corresponds to 1 USD (payable in USD, USDC, BTC, ETH or CKB), this may be subject to change. In addition, payments in crypto may not be available in certain jurisdictions.
1. Vulnerabilities which could easily crash the whole CKB network
2. Vulnerabilities which could easily cause consensus deviation
3. Vulnerabilities which could easily damage CKB economy
1. Vulnerabilities which could easily crash a CKB node
2. Vulnerabilities / Bad designs which could cause CKB network congestion with few costs
3. Incorrect implementation or behavior of CKB-VM / system scripts
1. Suboptimal implementation of CKB state storage mechanism
1. Any other important performance improvements for CKB
1. Any local RPC API crash
2. Any local command line crash
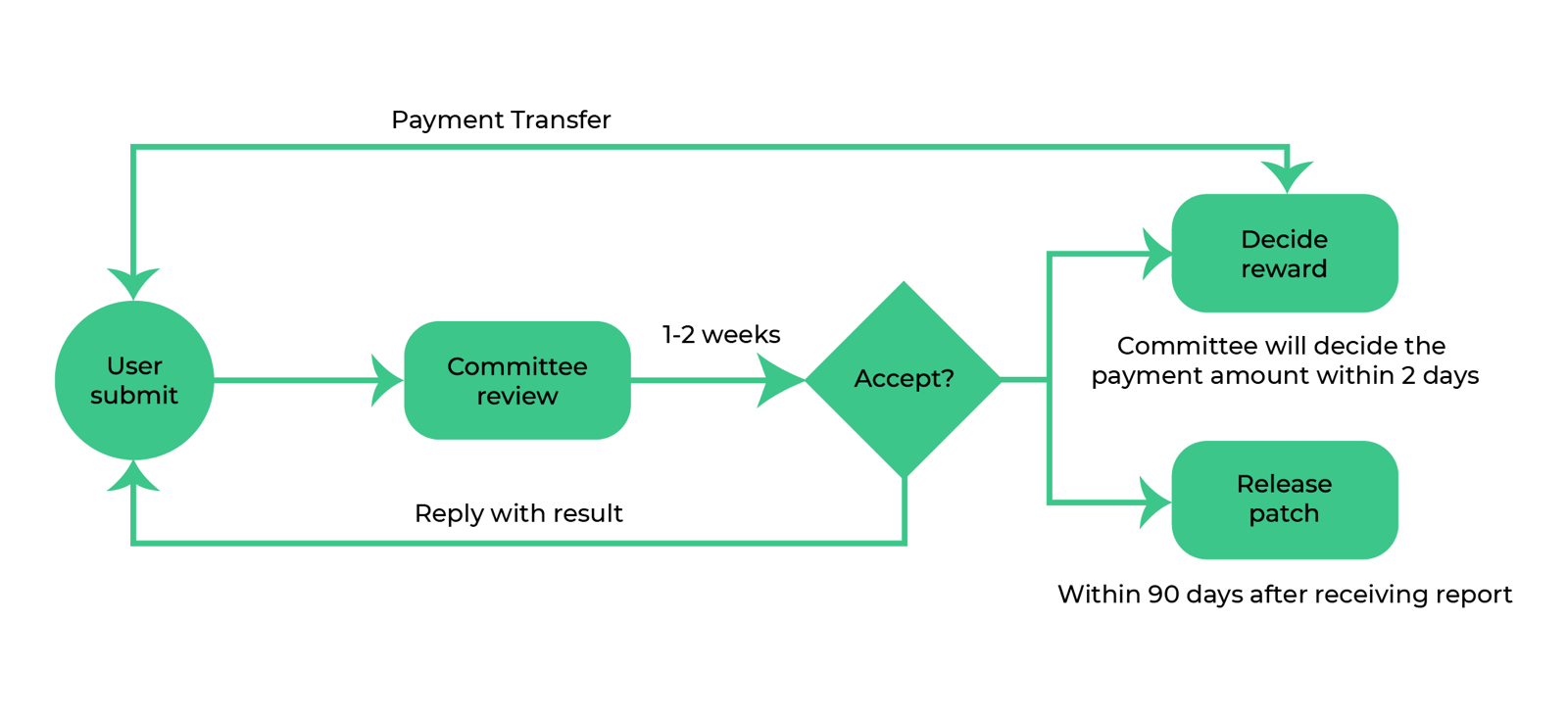
If you discover a vulnerability, please provide a report of the Vulnerability to Nervos at [email protected] and include your name, email address, company name (if applicable), a description of the bug, including your estimation of the potential impact to Nervos, and a description of the steps you took to identify the vulnerability.
The Nervos Bounty Program covers a broad scope, including but not limited to:
Protocols such as the consensus model, the economics model, the cell model, the p2p protocols, the PoW algorithms.
The security and integrity aspects of the protocol implementation.
Cryptographic primitives.
Account management flaws which would put end-user accounts at risk.
General software security vulnerabilities.
CKB Consensus Protocol CKB Consensus Protocol: It is a variant of Bitcoin's Nakamoto Consensus, that raises its performance limit and selfish mining resistance while keeping its merits. RFC
Economic Model Economic Model: The economic model of the Nervos CKB is designed specifically to preserve assets and other types of common knowledge. RFC
The PoW Hash Function Cell Model is a generalized programming model derived from the Bitcoin account model. RFC Request
Cell Model Cell Model is a generalized programming model derived from the Bitcoin account model. RFC
CKB CKB is the implementation compliance for all the protocols. Source Code
CKB VM CKB VM is a pure software implementation of the RISC-V instruction set used for VM scripting in CKB. Source Code
System Scripts System Scripts are the essential contracts developed by us. Since they will gain a widespread usage, the security of these scripts is essential to the system. Source Code
P2P P2P is a bundle of frameworks and protocols. We built a multiplexed p2p network framework which supports mounting custom protocols from scratch. We also defined and implemented the following protocols:
Block Synchronization
Compact Block Relayer
Transaction Relayer
Discovery
CKB Cli CKB Cli is a console tool to interact with CKB node. Source Code
Neuron Neuron is a desktop wallet. Source Code
Nervos websites
Duplicate reports of security issues, including security issues that have already been identified internally
Theoretical security issues with no realistic exploit scenario(s) or attack surfaces, or issues that would require complex end user interactions to be exploited
Issues determined to be low impact
Welcome to the Nervous Foundation Bug Bounty Program (the "Nervos Bounty Program"). If you believe you’ve found a bug or security vulnerability in compliance with the rules set forth in our Nervos Bounty Program Guide available at https://bounty.nervos.org, we encourage you to notify Nervos Foundation ("Nervos") in accordance with the guidelines below.
By participating in the Nervos Bounty Program, you acknowledge and agree that your participation is subject at all times to the terms set forth in these Nervos Bug Bounty Program Terms and Conditions (the "Terms").
The Nervos Bounty Program, these Terms, and any aspect thereof are subject to change or cancellation by Nervos at any time, with or without advance notice to you. Nervos may amend or update these Terms at any time by posting a revised version here or through other communications. By continuing to participate in the Nervos Bounty Program after such changes, you are indicating that you accept the new modified Terms.
You may only participate in the Nervos Bounty Program and make a submission of a security vulnerability report (a "Submission") if you are:
Over 18 years old;
Not a resident of, or currently residing in, a country or region against which the United States has imposed a general trade embargo (as of the date that these terms and conditions were last updated, such countries and regions are Iran, Cuba, the Crimea region of Ukraine, North Korea, and Syria); and
Not employed in any way by Nervos or any of its affiliates and an immediate family member of anyone thereof.
The Nervos Bounty Program applies to security vulnerabilities ("Vulnerabilities") within the Bounty Scope as set forth in the Nervos Bounty Program Guide. In addition, the Vulnerabilities must be found in code under the “Nervosnetwork” Github page, and not in the code of a third party.
You agree that your submissions to Nervos of Vulnerabilities you find comply with the Rules as set forth in the Nervos Bounty Program Guide.
You agree not to do any of the following in connection with your participation in the Nervos Bounty Program or otherwise:
Execute or attempt to execute any denial of service;
Interact with any third parties (which includes modifying or accessing data from such third party) if such third party has not consented to such action;
Spam or use any automated vulnerability tools that may generate large traffic volume;
Exploit any of the Vulnerabilities you discover in any way for any reason, including exploitation of any data uncovered by way of such Vulnerability;
Engage in social engineering (including “phishing”) of Nervos staff or contractors;
Intentionally violate any other applicable laws or regulations, including those prohibiting unauthorized access to data;
Physically attempt to gain access to Nervos property; and
Disclose any personal, financial, or location information publicly.
You agree to do all of the following in connection with your participation in the Nervos Bounty Program:
Inform us as soon as possible upon discovery of any Vulnerability through the submission process below;
Treat all information you receive, collect, or discover about Nervos, its affiliates, customers, users, or agents in connection with the Nervos Bounty Program (including all bugs and vulnerabilities) as confidential and not share any such information except with Nervos for the purposes of the Nervos Bounty Program; and
Make a good faith effort to avoid privacy violations and disruptions to others, including but not limited to unauthorized access to or destruction of data, theft, and interruption or degradation of our services.
Nervos reserves the right, in its sole discretion, to exclude certain categories of bugs or vulnerabilities from any reward in the Nervos Bounty Program.
If you discover a vulnerability, please provide a report of the Vulnerability to Nervos at [email protected] and include your name, email address, company name (if applicable), a description of the bug, including your estimation of the potential impact to Nervos, and a description of the steps you took to identify the vulnerability.
Properly submitted and documented in accordance with the submission process above and the Nervos Bounty Program Guide;
The first such Submission for the given Vulnerability.
Submissions will be reviewed by our security team. We aim to provide a response within a few days after receiving a Submission, but responses may be delayed based on the availability of the security reviewer and whether there are other more severe Vulnerabilities that our security team is currently addressing. If Nervos, in its sole discretion, determines that your Submission meets the criteria described above and that the Submission is the first for the given Vulnerability, Nervos will remit to you a reward, which depends on a number of factors, including but not limited to the type and severity of the Vulnerability, and as set forth in further detail in the Nervos Bounty Program Guide.
To be eligible to receive a reward, you must provide Nervos with accurate, complete and up-to-date information about you, including your name, email address, and any other information that Nervos reasonably requests, to allow Nervos to send a reward to you.
If you are located within the United States, you may not be eligible to receive tokens as rewards. If you are not eligible to receive tokens as rewards, any and all rewards you receive will be paid in USD, USDT, ETH or BTC only. If you are located outside the United States, you have the option to receive rewards in CKB Tokens. Before you receive a reward, you must sign and return to Nervos any additional agreements or forms as may be required and provided by Nervos, including without limitation, the Notice of Future Token Interest Award if your reward will be paid in CKB tokens. Nervos makes no guarantee of a token’s value in any currencies.
You are responsible for paying all taxes related to the rewards payments, if any.
You agree that any Submission will be the sole and exclusive property of Nervos. By submitting a Submission, you hereby irrevocably assign to Nervos and agree to irrevocably assign to Nervos all of your right, title, and interest in and to the Submission, including without limitation all worldwide patent rights, copyright rights, trade secret rights, and other proprietary or intellectual property rights therein.
By submitting a Submission, you represent that neither the Submission nor any use of the Submission by Nervos will infringe, misappropriate, or violate a third party’s intellectual property rights, or rights of publicity of privacy, or result in the violation of any applicable law or regulation, including export control laws.
You are not an employee, contractor or agent of Nervos, but are an independent third party who wants to participate in the Nervos Bounty Program. Nothing in the Terms is intended to render Nervos and you as joint venturers, partners, or employer and employee. Under no circumstance shall Nervos be considered to be your employer, nor shall you have any right as an employee of Nervos.
The bounty program starts on Oct 22 2019 and will end whenever the initial 1M rewards all being paid out.No end date is currently set. See the Nervos blog for the latest news.
Rewards may be paid out in USD, USDT, ETH, BTC or, in certain jurisdictions, CKB. Rewards are typically paid out after the submission has been validated, usually a few weeks later. Local laws require us to ask for proof of your identity. In addition, we will need your Bank account info/USDT/ETH/BTC/CKB address, as applicable.
For participants from within the United States, all rewards will be paid in USD, USDT, ETH or BTC only.
For participants from outside the United States, participants have the option to receive the rewards in CKB Tokens, subject to certain eligibility requirements described in the Program Terms.
If you discover a vulnerability, please provide a report of the Vulnerability to Nervos at [email protected] and include your name, email address, company name (if applicable), a description of the bug, including your estimation of the potential impact to Nervos, and a description of the steps you took to identify the vulnerability.
We ask that you give us reasonable time to investigate and mitigate an issue you report before making public any information about the report or sharing such information with others. We will try to review and respond to submissions as fast as possible. Feel free to email us at [email protected] if you have not received a response within two weeks following your submission.
Questions about the program or submission process? send an email to [email protected] and ask us.